|
|
| |
|
|
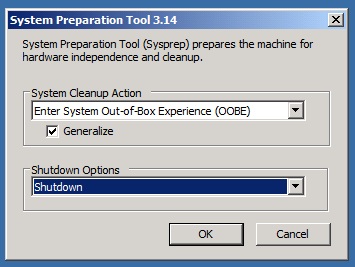
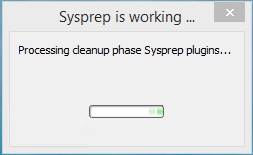
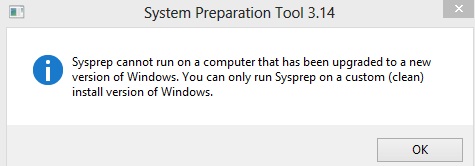
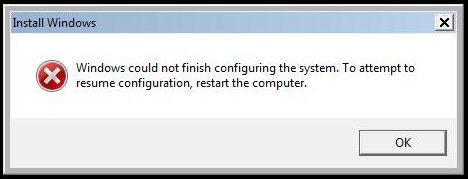
This is hacker project that should only be attempted by someone with such confidence in their technical abilities that it verges
on arrogance. It is a tale of multiple catastrophic failures that eventual resulted in success. If you lose focus, if you forget the goal,
if you momentary doubt your skill (Hudson: "That's it, man. Game over, man! Game over!") you will not get your old Windows 7
disk running again.
|